What is a Rootkit?
When you run an antivirus scan, you expect it will detect all kinds of malware and malicious code. However, rootkits are an insidious type of computer virus that are capable of remaining undetected, sometimes for years! They can allow hackers real-time access to your system, record and transmit your valuable information, and cause all sorts of havoc.
In this article, we’ll explore what rootkits are, how they work, and why they’re a significant threat to your digital safety. At the end, we will discuss some simple ways to stay safe from rootkits and other cybersecurity threats.

How Do Rootkits Work?
Rootkits are a specific type of malware that are particularly difficult to detect, allowing hackers to have access to compromised systems for weeks, months, or even years.
Concealment Techniques
Rootkits are notorious for their ability to hide themselves and their activities on your computer. Since they operate at the root level of your operating system, they can mask their presence from users and antivirus programs.
Their ability to hide extends beyond themselves and some rootkits can even disguise other harmful software!
Gaining Unauthorized Access
A rootkit infection typically results from hackers exploiting a security weakness in your system or, more commonly, social engineering attacks in which users voluntarily download and open infected files. This can come in the form of compromised email attachments or downloads, and even from infected USB-storage devices.
Evading Detection
What makes rootkit malware particularly dangerous is their ability to evade detection. They can intercept and alter system calls, manipulate data, all while staying under the radar of antivirus software. It isn’t uncommon for antivirus software to simply fail to detect rootkits, leaving your computer infected for long periods of time.
Common Types of Rootkits
Kernel Mode Rootkit
This is one of the most dangerous types of rootkits. It operates at the kernel level, which is the core of the operating system. Having access to the kernel means the rootkit has privileged access and can control anything on the system. It can intercept and manipulate calls to the operating system, hide its presence, and control system processes.
Kernel mode rootkits are challenging to detect and remove because of their deep integration with the OS.
User-Mode Rootkit
These rootkits operate at the application layer and are easier to install compared to kernel mode rootkits. They intercept and modify the behavior of standard system calls made by applications. While they are less powerful than kernel mode rootkits, they can still be used to steal user information and hide malicious activities.
They are generally easier to detect and remove than kernel mode rootkits.
Bootloader Rootkit
This type of rootkit, often called a bootkit, targets the master boot record (MBR) of a computer system, which is the program responsible for starting the operating system during the boot process. By infecting the MBR, the bootkit can load before the OS, gaining control of the system from the very beginning of the computer startup process.
This makes them particularly stealthy, as they can initiate their defense countermeasures before typical security software has been activated.
Firmware Rootkit
Firmware rootkits are embedded in the firmware of hardware devices, like your motherboard’s BIOS or a router’s firmware. They are extremely persistent, surviving even complete operating system reinstallation.
Because they reside in hardware, they are difficult to detect and remove without specialized knowledge and tools.
Application Rootkit
These rootkits target specific applications and modify their behavior to avoid detection. They can be used to log keystrokes in a specific application, steal data, or provide unauthorized access to the application’s features.
Because they operate within the confines of an application, they are typically more limited in scope compared to system-level rootkits.
Memory Rootkit
Memory rootkits reside entirely in your computer’s RAM and thus leave minimal traces on your computer’s harddrive. This type of rootkit is effective in evading detection because it disappears upon reboot, since RAM is volatile memory, which does not persist through power cycles.
However, this also means that they need to be reinstalled each time the system starts, which can be a limiting factor in their use.
Real World Rootkit Examples
Stuxnet (2010)
Stuxnet emerged as a groundbreaking and sophisticated rootkit targeting Iran’s nuclear program, particularly the Natanz uranium enrichment facility.
Widely believed to have been developed by the United States and Israel, although never officially confirmed, Stuxnet represented a new level of cyber warfare. It’s thought to have been in development since at least 2005 and remained operational for years before its discovery in 2010.
The rootkit specifically targeted industrial control systems used in the Iranian nuclear program, causing significant damage to the centrifuges used in uranium enrichment and is estimated to have destroyed over 1,000 centrifuges and significantly set back Iran’s nuclear ambitions.
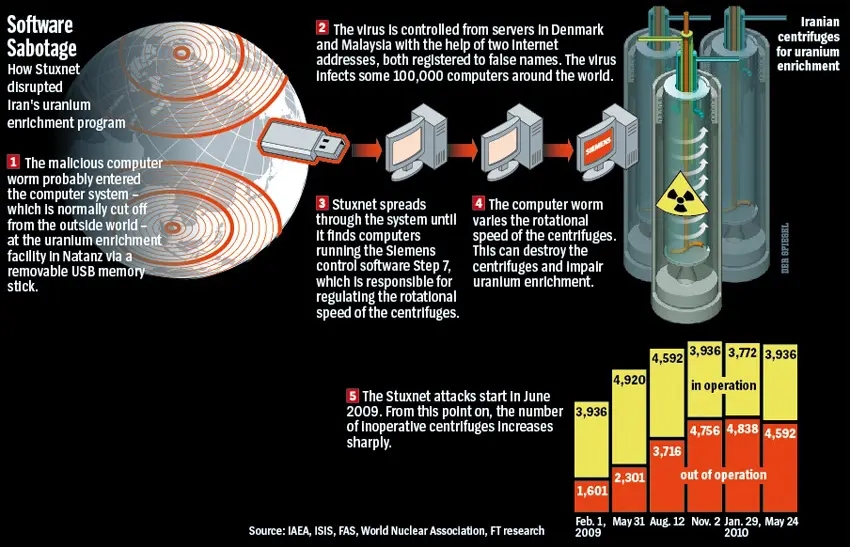
Image from https://cyberhoot.com/cybrary/stuxnet/
Ryuk Ransomware (2017 – Present)
First identified in 2017, Ryuk Ransomware has been a persistent threat, often using rootkit capabilities to gain control of victims’ networks. Although the creators of Ryuk are not definitively known, it is believed to have ties with North Korean hacking groups or Russian criminal organizations.
Ryuk is known for targeting large organizations, including healthcare, government, and private sector entities, demanding large ransom payments. It has caused extensive damage, including disrupting operations and causing financial losses.
Notable attacks include crippling the IT infrastructure of several U.S. newspapers in 2018 and disrupting the operations of Universal Health Services in 2020.
DarkTequila (2018)
Uncovered in 2018, DarkTequila was a complex, multifaceted malware operation that predominantly targeted users in Mexico, likely developed by cybercriminals based in the region. The rootkit had been operational for years, possibly since 2013, before it was detected, and specialized in stealing banking credentials and personal data without being detected.
The malware was often spread by infected USB flash drives – driving home the importance of being very wary about plugging any suspect drives into your PC!
The damage done by DarkTequila included financial fraud and significant data breaches, affecting private individuals and businesses alike.

Why Rootkits are Dangerous
Computer Performance Issues
Rootkits can drastically affect the performance of a computer. They often consume a lot of system resources, leading to noticeable slowdowns, system crashes, and unreliable application behavior.
This not only hinders productivity but can also be a sign of deeper, more damaging activities happening in the background, like data extraction or additional malware installation.
Persistent Threat
Due to their ability to hide and evade detection, rootkits can remain on a system for a long time, either causing ongoing damage or waiting quietly for the opportune moment to strike. They can disable security software and update themselves to evade newly developed detection methods, making them a persistent threat that’s hard to eradicate.
Data Security Risks
The presence of a rootkit in a system poses severe risks to data security. Rootkits can function as keyloggers, helping attackers steal sensitive information such as login credentials, credit card and bank account details, personal information, and confidential corporate data.
The stealthy nature of rootkits means that data theft can occur over extended time periods without detection, leading to significant privacy violations, identity theft, financial fraud, and corporate espionage.
Loss of Control
One of the most insidious aspects of rootkit attacks is the unauthorized control they grant cybercriminals over the infected system. Attackers can use rootkits as a backdoor to remotely execute commands, alter system configurations, install additional malware, and manipulate system functionalities, all without the user’s knowledge.
This loss of control can turn your computer into a tool for perpetuating cyberattacks like spreading malware, launching distributed denial-of-service (DDoS) attacks, or participating in botnets.
Not sure what a DDoS attack or a Botnet is? Check out our past articles exploring how DDoS attacks work and what you need to know about botnets to learn more!
Simple Prevention Tips
Regular Software Updates
Keeping software up-to-date is crucial in the fight against rootkits. Software developers regularly release updates that patch security vulnerabilities. By ensuring your operating system and applications are current, you can close the gaps that rootkits exploit.
Set your system to update automatically or make it a habit to check for updates frequently.
Invest in Reliable Security Software
A robust antivirus or anti-malware software is your first line of defense against rootkits in particular and malicious software in general. Look for software that specifically includes rootkit detection and rootkit removal capabilities. These security tools can scan for and identify suspicious behavior, helping to catch rootkits before they embed themselves deep within your system.
Additionally, ensure your security software is always kept up to date with the latest malware definitions.
Utilize Effective Firewalls
A firewall acts as a gatekeeper for your computer or network, controlling incoming and outgoing network traffic based on security rules. It’s an essential tool in preventing unauthorized access to your system, which can help stop rootkits before they infiltrate your computer.
Operating systems like Microsoft Windows and MacOS ship with built-in firewalls. Ensure that these are enabled – as they won’t do you any good if they have been turned off!
Be Aware of Phishing Attempts
Many rootkits (and other types of computer viruses like trojans) find their way onto computers through phishing – deceptive practices that trick users into revealing sensitive information or downloading malware.
Always be cautious with emails or messages from unknown sources. Avoid clicking on suspicious links or downloading attachments from untrusted emails. Educate yourself and your team, if applicable, about how to recognize phishing attempts.
Stay Informed
The landscape of cybersecurity threats, including rootkits, is constantly evolving. Staying informed about new threats and trends in cybersecurity can significantly improve your ability to defend against them.
By reading this article you’re already doing a better job of staying informed than the average user, and we urge you to continue following reputable cybersecurity news sources and subscribe to security bulletins from trusted organizations!

Keep Your System Safe
Rootkits pose a serious threat to our digital security and the difficulty involved in detecting them makes prevention essential. Understanding what they are, how they operate, and the dangers they present is the first step in safeguarding yourself against these threats.
Keeping your computer and software updated, staying vigilant against phishing and social engineering threats, and using an antivirus which includes anti-rootkit capabilities are all essential for keeping your computer safe.
If you suspect that your computer may have an infection, or just want to make sure that your protection is adequate, we provide comprehensive computer virus detection and removal services for the Columbia Midlands.
