The Old New Face of Digital Scams
We get used to things moving and changing so fast due to digital technology, that we often don’t notice how we might fall for old-school tricks that have been around for decades. For example, even the earliest days of email were full of scams that sought to get enough information from an unsuspecting user to hack their bank accounts. And that doesn’t even cover how hackers often gather credit card numbers, log in names, and passwords to sell to the highest bidder. These days, this kind of hacking is trivial, so much so that sites on the dark web offer tools (with help desk support) that help hackers launch attacks.
These days, hackers still use emails and fake websites to trick users into turning over their private data through a technique called “phishing”.
And while many of us probably think we are too smart to fall for an obvious scam, phishing attacks are actually quite sophisticated. The FBI claimed in 2017 that phishing scams could cost businesses upwards of 5 billion dollars. Even those seemingly most familiar with the newest technologies–students–are some of the most likely targets for phishing attacks.
The key to avoid being a victim of phishing attacks is to understand what they are, and how to avoid them.
What is phishing?
“Phishing” is a term used to describe social engineer techniques used by hackers to gain the trust of users through official-looking communications, typically through email. These communications will often appear as an official email from an organization, like a school or a bank, and direct the receiver to provide personal data. Sometimes, the email will ask the user for information directly. More subtle phishing attempts will copy branding and official emails from prominent companies. Attackers will simply change links in the emails to direct users to fake websites (also designed to mimic a company brand) where they will ask users for their login information.
Much like its namesake activity, hackers will “fish” for victims in a pool of unsuspecting users. Typically, there are two different approaches to fishing:
- General phishing involves sending out hundreds, or even thousands, of emails to random users. These users typically don’t share much between them demographically, other than they use email. Because of the random nature of these attacks, chances are 95% of the receiving users will not fall for the trick. But, that leaves 5% of thousands that do, and that can mean access to a large volume of bank and credit card accounts (among other possibilities)
- Spear Phishing is a targeted form of phishing. A group of hackers might gain access to a mailing list, say from a university. They then create emails crafted to look like the official communications of that organization, send it to the only people who would have reason to get that kind of communication (students, teachers, and staff) and fool them into turning over access to their accounts. Spear Phishing is less effective for large-volume scamming, but it can produce more targeted results from people with sensitive, business-related data.
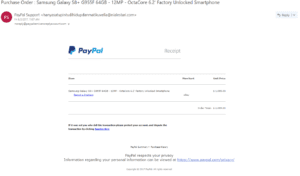
Phishing Email Examples
Here is an example of an email crafted for phishing purposes. In it, the sender has taken on the identity of PayPal. The email itself is a close replica of an email the real PayPal might send out, with specific information changed or falsified to get a response from the reader.
Some portions of the email signal that it is a fake right away. Most noticeably, the sender of the email is not actually from a PayPal email address (even though they tried to fake, or “spoof”, the address). But the rest of the email looks pretty authentic. More than that, it raises the concern that the user’s account has been accessed without their authorization. If someone received this email had a PayPal account tied to that email, and they got a notice that someone changed their security questions, it would immediately raise red flags.
What an email like this counts on, is that the reader will panic. That concern leads the reader to glance over the document, and to ignore certain aspects of it that would mark it as falsified. In that case, they may send the hacker the information requested before even thinking about it.
How Do I Avoid Getting Hooked by a Phishing Attack?
Identifying a phishing attack isn’t always easy if you don’t stop to take in all the information. If you follow some basic precautions, however, then you can typically avoid any issues.
- Check the email address of the sender. Individuals phishing for information via email will use different tricks to make themselves look like the company they are mimicking. In the above email example, we saw how someone can spoof an address enough to get by an unsuspecting reader.Before you click anything, check the domain of the email sender. For example, the email address “noreply@paypalservicenoreplyaccount.com” doesn’t actually come from PayPal. Some companies do host several email domains for different purposes, but when the domain is long, odd-sounding, or only tangentially related to the company it represents itself as, you have good reason to suspect its validity.
- Read every email you receive carefully. Some sure signs that an email is falsified is if it presents itself as a professional communication but contains numerous typographic errors or awkward phrasings. Likewise, pay attention to what the sender is asking you to do. No company is going to request sensitive information via email. So, if an email ever involves providing personal information (typically for “verification purposes”) like your username and password, account numbers, address, or phone number, then it is almost certainly a phishing scam.
- Check the domain of any link in the email. More sophisticated phishing attempts will involve copying in already-existing email template from an organization and changing the source links in the email to malicious websites. Since link text doesn’t have to match an actual URL, phishers can hide the location of the website from readers who don’t read closely. And, with modern URL shorteners like bit.ly, it’s become even easier to hide a URL from you. Any professional organization looking to reach out in official business will rarely, if ever, use a non-domain specific or shortened URL. When you hover your mouse over a link in your browser, however, the browser will show you the full URL somewhere in the window. If that URL is an odd or unencrypted link to a third-party website, then don’t click it.
- Understand how domains work. Some hackers will work hard to make a domain look similar to a major company’s domain, even though they aren’t the same. For example, a hacker group might ask you to follow a link that looks like this: “http://paypal.hrsecurityhelp.com”, This looks somewhat legit at first glance, because there is a “paypal.com” domain. However, this link actually points to the domain “hrsecurityhelp.com” and not PayPal. In domain registries, the phrase directly before the “.com” is the actual domain, and anything before that is a subdomain, and not the other way around. This subtle trick can make a URL seem legitimate, even as it directs users to a third-party site.
- Try to make direct contact with the company in question. If you’ve received an odd email from a company asking for questionable information, nothing will address the issue quicker than reaching out directly via phone. Do not, however, call from any information provided by the email or a questionable site. Point your browser directly to the company’s site (typically the company’s name plus a “.com”.) Company names are usually trademarked and their domains reserved, so it is unlikely that a third-party hacking outfit would own “paypal.com”, for example.
- Never download attachments from anyone but trusted sources. Hackers might use a familiar-looking brand to get you to open attachments in emails. Don’t. It’s just a bad idea and invites all sorts of security issues to your computer, including data theft.
- Don’t rely on https encryption. Common knowledge states that secure, legitimate sites will use Secure Socket Layer (SSL) encryption for browsers exchanging sensitive data. You can tell if a site uses this encryption if the URL starts with a “https:” instead of a “http:”, and your browser shows a lock symbol (or more) near the URL. The idea was that certificates for encryption showed that the owner of the site was exactly who they said they were (and you could check that right in your browser by clicking the lock). However, it is now estimated that nearly one quarter of phishing sites are now using https encryption. Bottom line, if you don’t trust the site, don’t give them information.
For phishing prevention information on social media platforms, check out this blog.
Why Phishing Still Works Today
Since phishing is a social engineering attack, it works on the premise that we are busy, distracted, and somewhat undereducated about cyber threats and how they work. Hackers look for ways to pass themselves off as other organizations in the hope that, even if it doesn’t work most of the time, it will work at least some of the time–and it really only has to work some of the time for a hacker to gain access to sensitive information, money, and credit cards.
What’s more, hackers are evolving faster than even tech-savvy students. As universities host student emails, hackers can gain access to emailing list and build highly sophisticated spear-phishing campaigns that will trick students not familiar with email or forgery. These campaigns can include letters that even use a university’s branding and letterhead.
So, don’t fall for the trap. If an email asks for personal information, comes from a shady source, or directs you to a third-party site, just delete it. Keep your information safe and avoid the headaches of being hacked.
