What happens when you click on a phishing link?
If you have an email address then you surely have received unsolicited messages that seem a little fishy. These messages tell you about prizes you have won, unfamiliar bank accounts that are overdrawn, or even the classic Nigerian prince looking for someone to help move their millions.
Most of the time these emails are strange enough to set off alarm bells – but sometimes they seem just plausible enough that clicking that link seems like a reasonable risk. After all, what is the worst that could happen?
Today we’ll look at how to identify phishing attacks and examine their risks. Finally, we’ll cover what you should do if you have accidentally opened one of the malicious links contained within these emails and suspect your computer has been infected by a virus or malware.
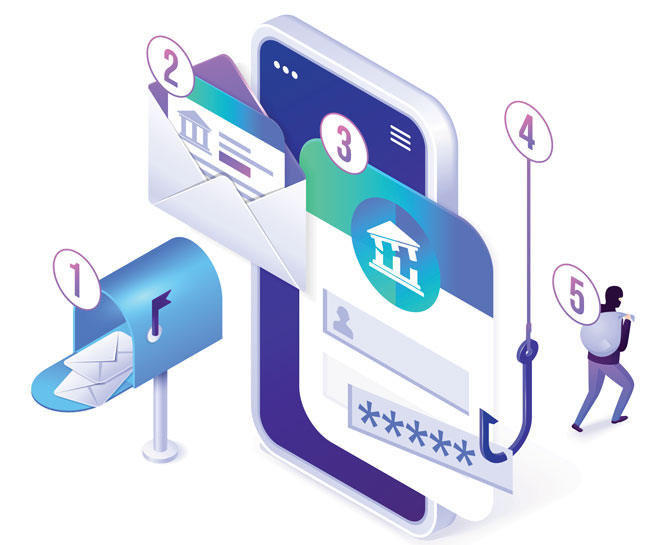
What is phishing?
Phishing refers to the practice of sending emails which pretend to be from a trustworthy source in an attempt to get people to divulge their personal and private information. Phishing emails take many forms, ranging from fake lottery or sweepstakes notifications to fake credit card alert emails.
Note: The word ‘phishing’ is a portmanteau of fishing and phreaking – a term coined in the 1970s to refer to hackers who would exploit vulnerabilities in the phone system to make free calls.
Unopened, the emails themselves do no harm – but if a user believes that the message is legitimate then they may click on links contained within the email, exposing themselves to risk.
Smishing
While email based phishing is the most common form – smishing or SMS-text message based phishing is on the rise. Never open unsolicited links or download file attachments that arrive via text message.
Spear Phishing
Possibly the most dangerous form of phishing, spear phishing uses messages that seem to come from a trusted sender. These attacks are often orchestrated by breaching a legitimate email address or using spoofing techniques to send emails which appear to be from a trusted sender.
These attacks are harder to defend against as users are going to be more likely to click on a link or download an attachment from a familiar sender.
Social Engineering Attacks
Social engineering exploits people instead of computer vulnerabilities and can be paired with phishing to create very effective cyber attacks. One way that these attacks can be executed is by sending emails which your business would expect – for example sending a job application which includes an attachment or link.
If your business is currently hiring you may think little of opening an email with this information! For this reason it is always essential to scan files with an updated antivirus before opening them and to be wary of suspicious links, no matter the source.
How do you know if you’ve clicked on a phishing link?
While it can sometimes be difficult to tell if you’ve clicked on a phishing link, here are some red flags to look out for:
- Spelling and Grammar – Phishing sites are often hastily put together and may contain spelling or grammar errors. Be on your guard if you notice spelling mistakes.
- Odd Website Appearance – While businesses update their website from time to time, if a page doesn’t look right, listen to your gut and don’t provide any sensitive information until you’ve verified the site is authentic.
- Unusual URL – Most phishing attempts work by using a site that pretends to be a legitimate site. If you think you should be at Amazon.com but the URL says Amaz0n.com, something is wrong!
- Page isn’t using HTTPS – Most of the web uses secure SSL connections which many browsers identify with a lock icon in the URL bar. Additionally, the URL itself will begin with HTTPS:// instead of HTTP://. You should always avoid inputting your sensitive data into web pages which are not using a secure connection.
What happens if you open an email with a phishing link?
In many cases, phishing emails are hard to identify from their subject line alone. This means you may find yourself looking at an opened email with suspicious links or attachments and wondering if the damage has already been done.
The good news is opening an email without clicking on links or downloading attachments is unlikely to result in any harm.
If the email has arrived at your personal address, your best bet is to report the email as a phishing attempt to your email provider so they can block the sender in the future. If the email has come to your work email address, you should contact your IT department so they can take steps to protect your business’s network against future phishing attacks.

What happens if you click on a phishing link?
Despite our best efforts, phishing scams can be quite effective. A study in 2021 found that 3% of employees will ultimately click on a phishing email link – possibly exposing their organization to risk.
Every phishing attempt is slightly different – but these are the most common risks that networks face:
A hacker might receive information from or about you
A typical phishing website will look like a login page – usually for a financial institution, email provider, or other legitimate online service.
Any login credentials, personal data, or credit card numbers you provide here will be sent to the cyber criminals who created the phishing attack. In some cases the login credentials may actually be passed along to the real website and you will be successfully logged in, while in other cases you may simply receive an error message.
Similarly, some pages will request credit card information, social security numbers, or other sensitive details.
The attachment may try to run a macro or scripts
A common way that hackers breach your system with phishing links is by using malicious macros embedded in Word documents or PDFs. Macros are automations which use pre-programmed key presses and mouse clicks to accomplish a specific task – in this case usually something nefarious.
Software developers recognize the potential for macros to be used maliciously, so most document readers will ask you if you wish to enable macros or scripts when they are present. Never enable macros, even if the file comes from a trusted source.
There may be limited circumstances where your line of work requires that you allow macros – but these are going to be highly specific circumstances. The vast majority of us will never need to enable macros and allowing them to operate is an unnecessary risk.
Malware may be installed on your device
In extreme cases, phishing sites may go a step further and install malware on your computer. This is more common when attachments are downloaded and opened – but browser vulnerabilities exist that can result in malicious files being surreptitiously opened, even without user action.
Your network and contacts may be exploited
Whether the phishing attack installs malware software or simply steals your email account credentials, the attack often is just beginning. Using information obtained from spyware or helpfully provided by an unwitting victim, the attackers can then launch even more damaging attacks against your network or contacts.
What to do if your device has been compromised
As soon as you realize that you may have accessed a phishing site, it is important to take action:
Disconnect your device
Quarantining your system can be a highly effective way to limit the damage of a variety of cyber attacks including ransomware attacks. If your computer has a wired internet connection, disconnect it immediately. If it is connected to your wireless network, power off the connected device and use a second device to change your wi-fi network password.
Change passwords and credentials
Using a non-compromised device, immediately change any passwords that may have been exposed in the breach. The most critical passwords to keep control of are email accounts and financial accounts, and these should be secured first.
Monitor or freeze your credit
Identity theft is one of the most serious risks of phishing so it is prudent to keep a close eye on your credit. While not always convenient, freezing your credit with the three major credit bureaus (Experian, TransUnion, and Equifax) is a great way to protect yourself from unauthorized new account creation.
Scan your system
Run a full system scan with antivirus software to ensure that no malware was added to your system. Windows computers ship with the antivirus program, Microsoft Defender, and there are numerous reputable anti-malware programs available from third parties.
Back up important files
Keeping backups of important files should already be a part of your cyber security protocols – but if it isn’t, now is the time to make backups. Save any irreplaceable or mission-critical files to an external harddrive. This will protect you in the event that a ransomware attack compromises your system and makes your files inaccessible.
Speak to a data breach expert
For maximum peace of mind, it is a good idea to contact an IT service who offers data breach protection. They will be able to help ensure that your system doesn’t harbor any lingering signs of intrusion and protect against future attacks.
An Old Problem That Isn’t Going Away
Scammers have been using phishing attacks since the earliest days of the internet, and while the subject lines may have changed over the years the attacks haven’t. You should always treat unsolicited emails with suspicion, and in particular should be wary of links and attachments.
If you have already opened a suspicious file or clicked on a link that took you to an ersatz login page, then your system may be at risk. Contacting a local IT professional for virus and malware removal service is the most effective way to ensure your computer stays safe.
