How to Set Up A Secure Home Network
There was once a time where home networks were mostly made up of wired devices and your router’s role was largely relegated to splitting the signal between ethernet cords. Today however, routers are tasked with heavy lifting, connecting potentially dozens of wireless devices ranging from smart toasters to printers to game consoles.
As wireless proliferation has become the norm, the importance of securing these devices against hackers and malicious attacks has grown. Today we all casually transmit our most personal information from our home Wi-Fi network and thus it is essential to ensure that your home network security is properly implemented.
In some cases your default router settings are a good starting point – but the following tips will maximize your network’s cybersecurity:
It all starts with the wireless router
Enhancing your home network security begins at your router, whether you lease your router from your internet service provider or have purchased your own.
For those who have leased their router from their ISP, it isn’t uncommon for the router and the modem to be integrated into one unit, but for the sake of security functionality there isn’t a significant difference between the two types for home use.
The reason your router is the lynchpin of your network security is simple: it is your gateway to the internet and connects each of your network devices to one another. If it is compromised then your network traffic can be monitored or malware can spread across your local network, infecting all of your connected devices.

Change your router’s default username & password
This simple step is absolutely necessary and failure to do so gives any would-be attackers easy access to your network. Wi-Fi routers ship with default usernames and passwords to allow for easy setup, and the router manufacturers universally instruct their customers to change the password after installation. Unfortunately, many people ignore this step at their peril!
The problem with not changing your default username and password is that these default values are public knowledge. Even if hackers don’t know the make and model of your router, it is a simple task to employ a ‘brute force’ attack where a program tries every common default password and username combination.
Before we move on, it is important to distinguish between your wireless network’s password and your router’s password. Your network password will be what you use to log into your Wi-Fi while your router’s password allows you to access your router’s security settings, update firmware, and more.
Usually you can access your router’s setting page by using your web browser to access the IP address 192.168.1.1 or 192.168.1.254, although this gateway address occasionally varies by manufacturer.
While we recommend that you change your default wireless network name (SSID) and Wi-Fi password, here we are specifically referring to your router’s administrator settings login information.
As with all passwords, you should avoid easily guessed phrases such as ‘password,’ ‘12345678,’ birthdays, pets names, or anniversaries. We recommend using a password manager to create a strong password and to store that password for future use.
Enable WPA3 Encryption
Wi-Fi Protected Access 3 (WPA3) is the current generation of network encryption, and has been included on commercially available routers since 2018. It is common for routers to ship with both WPA2 and WPA3, allowing for easier backwards compatibility, but sacrificing some security in the process.
Note: If you are renting your router from your ISP it is possible that your router will only support WPA2. WPA2 is better than nothing, but this encryption protocol was released in 2004 and is less secure than its newer replacement.
Enabling WPA3 is usually as simple as clicking a toggle switch in your router’s security settings. This is the ideal sort of security upgrade as turning it on shouldn’t noticeably change your browsing experience – it will just make your network much harder for attackers to breach!
In some cases you’ll be able to choose between AES and TKIP security protocols (available for both WPA2 and WPA3). We recommend selecting AES as it is generally regarded to be a more secure encryption protocol and doesn’t come with any downsides over TKIP.
If your router only offers you WPA or WEP as encryption options then now is the time to get a new router! These older encryption standards can be cracked in seconds using off-the-shelf computers and easily obtainable software. When purchasing a new router make sure that it supports the WPA3 protocol as it is far superior to WPA2.
Change the name of the wireless networks (SSID)
All Wi-Fi networks have an SSID (short for the rarely used expanded version: service set identifier) or name which you use to access it. Usually the default name of your network will include the brand name of the router, or your ISP’s name, plus a string of numbers.
Besides being difficult to remember and hard to tell apart from your neighbors’ (assuming they’re using the same ISP as you), using the default SSID poses security risks too. Just by looking at your network’s name, hackers will be able to tell what brand of router, and possibly the exact model, your network is running on.
With this information they’ll be able to identify which model-specific vulnerabilities to try, or even gain access to your router’s administrator settings if you’ve forgotten to change them from their defaults!
Changing your network SSID will make it easier to remember which Wi-Fi network is yours and make it more challenging for attackers to know what hardware you’re using.
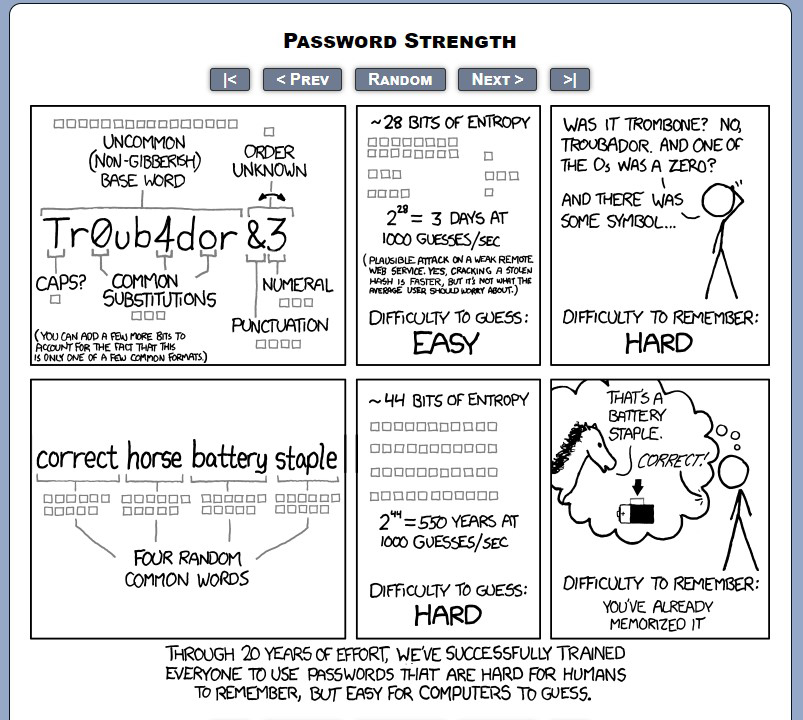
While you’re at it, we recommend changing your network password as well. The long strings of letters and numbers that come from the factory are secure, but they are horribly inconvenient to remember. Instead put three or four random words together to create a strong, but easily remembered password.
Disable Remote Management
Remote management (sometimes called remote access or remote administration) is a feature of questionable utility for casual home users. This feature does exactly what it says it does: allows you to make changes to your router’s settings from anywhere with an internet connection.
The vast majority of users will never use this feature – instead only making changes to their router settings from home while connected directly to their local area network (LAN).
If this were simply an unused feature this wouldn’t be much of a problem, but by allowing remote access you are giving hackers an easy point of attack. When disabled, your router simply won’t accept login attempts from outside of your home network, making any would-be hacker’s job much more difficult.
Most routers ship with this option disabled – but it’s best to check your router settings to be sure!
Make sure that the hardware firewall is enabled
Today, all Windows and Apple computers ship with built-in firewalls to help keep your data safe. This is great – but does little to protect the other devices on your network. The good news is that most routers include their own firewall as well.
Enabling your router’s firewall is generally a simple affair – simply log into your router’s admin settings and find the toggle for the firewall. In general, enabling the firewall shouldn’t cause any problems – although if you host your own server you may need to modify the firewall settings to keep everything working smoothly.
Create a guest network, and a network for IoT devices
A great feature which has made its way into even inexpensive routers is the ability to set up multiple networks. Since all devices connected to a single network can communicate with one another, any new devices which connect to it pose a risk to the network’s integrity as a whole.
Certain types of malware are capable of spreading to devices they share a network with, so keeping outside devices isolated keeps your network safe.
Rather than open up your network to friends, relatives, and HVAC repair technicians who need Wi-Fi to send you your invoice, a guest network puts them into a walled garden where they can’t do any harm. From the guest network they’ll have internet access, but they won’t be able to see your network resources like printers or networked harddrives, or any other devices that may happen to be on the guest network..
In some cases guest networks settings are limited to choosing a password and maybe an SSID, but in more full-featured routers you may be able to further refine what guests can access. If possible, it is best to disallow guests from accessing your router’s settings – there are next to zero possible scenarios where your guest will need this access and it prevents hackers and malware from gaining control.

A feature which is becoming more common in home routers is the ability to create a dedicated network just for your Internet of Things (IoT) devices. IoT refers to any device that connects to the internet which isn’t your mobile device or computer, like Ring doorbells, Nest smoke alarms, and Roomba vacuum cleaners.
While these smart home devices need to be connected to the internet to work, they don’t need to be a part of your home network! IoT devices are commonly targeted by hackers as their operating systems are usually not as secure as phones and PCs, and can be used to create botnets which spread malware and steal information.
By putting these devices together on their own network you will keep your devices which contain your private data safe from prying eyes. In a perfect world, your router will have the ability to create a network just for these devices, but if it doesn’t then the guest network setting is an acceptable substitute.
Note: Some devices, like wireless printers, may need to be on the same network as your computer in order to work correctly. Others, like smart appliances which you access via an app, typically only require an internet connection.
Disable UPnP and WPS
Two features that most routers still include but should definitely be disabled are Universal Plug and Play (UPnP) and Wi-Fi Protected Setup (WPS). These features were intended to make connecting new devices easier, but this functionality comes at a great cost to your network security.
UPnP is a feature which enables devices to automatically establish the connections they need to communicate. This may involve enabling port forwarding, modifying DNS settings, or changing other similar settings. The trouble with UPnP is that it is a black box – you as the external user don’t get to see the process happening. This allows infected devices to make unwanted changes, exposing your entire network to risk.
In most cases disabling UPnP will not result in any disruption to your home network – although you may need to manually enable port forwarding for VoIP or similar services.
WPS is a feature which allows you to connect devices to your router without having to type in a password. This seems like a great way to keep your password safe – but the problem is that early versions of WPS have severe security vulnerabilities.
WPA3’s version of WPS is far more secure than earlier versions, but usually when using WPS on WPA3 your router will simultaneously enable the less secure WPS for WPA2 to facilitate backwards compatibility. For now, it is best to just completely avoid this feature.
Regularly update your router’s firmware
You know how your computer and phone are always asking you to perform another update? Well, your router needs updates too – it just tends to be less pushy about asking for them! Just like your computer and phone, these updates usually include bug fixes, performance tweaks, and (most importantly) security fixes.
Some routers make the update process as easy as enabling automatic updates in the router’s settings, but many will require a bit more work on your part. Often you’ll have to download the appropriate file from the router manufacturer’s website and then upload that file from your computer to the router. The process isn’t complicated per se – but less seamless than updates for your laptop or phone.
The good news is that most router manufactures only release a couple firmware updates per year so this isn’t something you’ll need to put on your weekly to-do list. The bad news is that since this task needs to be performed so infrequently, it is easy to forget about.
Conclusion
Ultimately, securing your home network is just one of the necessary steps to protect yourself and your data online. Modern routers include lots of built-in technology which helps keep attackers at bay – although in many cases these features need to be manually enabled. Similarly, some ‘convenience’ features that come with your router pose security risks that likely far outweigh their benefit.
At Bristeeri Tech we offer a complete home network security solution, keeping your network safe from intruders. Protect yourself today by following our suggested tips, or let us help you get started!
